Strategic Steps: Building a Business Ransomware Incident Response Plan

Businesses today use technology a lot. It helps them do their work every day. But sometimes, malicious people try to attack them using the internet. One of the worst kinds of attacks is called ransomware. It’s like a digital hostage situation where hackers lock up a company’s elemental files and demand money to let them go. That can hurt a company in more ways than you can imagine.
First, the company has to stop working their usual routine to deal with the situation. Secondly, their secrets are in the wrong hands, and who knows what the enemy could do with that information? Lastly, the company will incur huge financial losses in one way or another.
Luckily, all that can be avoided with a good Business Ransomware Incident Response Plan. This strategy helps to prevent cyber attacks and guides on what to do in case of an attack.
This guide is here to help you make that arrangement. It will show the necessary steps that can be followed to keep the company safe from malware threats. Also, learn about MROCs In Business with this guide.
Understanding the Ransomware Threat Landscape
Before we dive into the approaches to deal with the problem, let’s understand what it is. Think of ransomware as a sneaky computer virus. It sneaks into the computer and locks up all the decisive files, like photos and documents.
How does it get in? Sometimes, it tricks users into letting it in by clicking links in their emails or downloading infected stuff. It can also come from shady websites or infected software. Once it’s in, it locks up the files and demands money to unlock them or let the user use their computer again. It’s like a digital bully holding the stuff hostage until you pay up. But don’t worry, we’ll talk about the ways to keep the computer safe from it.
The Impact of Ransomware Attacks on Businesses
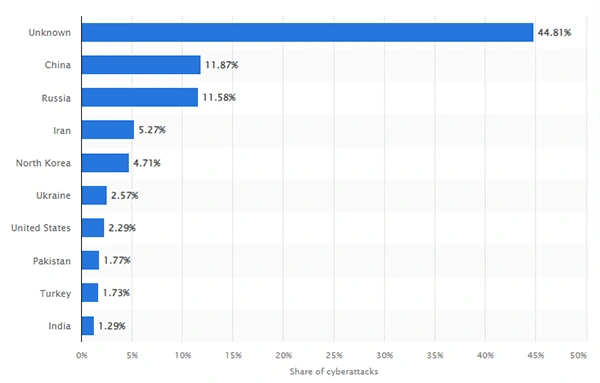
(This graph shows the countries initiating the highest share of cyber incidents with political dimensions from 2000 to 2023).
These attacks impact businesses in so many ways. Below are some of them.
- They disrupt organizational operations, causing delays and reducing productivity.
- Loss or corruption of data occurs, damaging a company’s reputation and leading to legal trouble.
- Dealing with malware is expensive, involving payment, clean-up, and rebuilding trust with customers.
- To minimize the impact, companies should have an approach in place.
Building a Ransomware Incident Response Plan: Strategic Steps
Making a ransomware response plan needs careful steps. If you do everything right, you can defend the businesses against it and reduce its harm. Let’s look at each step closely.
Conduct a Thorough Risk Assessment
To create an incident response plan,
- Assess Risks: Check for weak spots in the systems and understand potential impacts.
- Identify IT Vulnerabilities: Find where the systems are weak and the probability of intrusion.
- Evaluate Integral Assets Weaknesses: See if vital things like input and systems have problems like old software or weak passwords.
- Consider Financial and Data Impacts: Consider the amount of money you could lose and how sensitive the information is.
- Understand outside threats: Know what hackers might do.
- Stay Updated on Ransomware Trends: Keep learning about new tricks.
- Prioritize Response Efforts: Focus on what’s most urgent and update the plan regularly to stay strong against attacks.
Establish Clear Protocols and Procedures
After completing the risk assessment, the next step is establishing clear protocols and procedures for dealing with such accidents. This involves;
Forming a Response Team
- Bring together a group of people from different areas like IT (Information Technology), cybersecurity, legal, and executives.
- Each person in the team has a specific job and level of authority to make decisions.
Creating an Incident Response Plan
- Make a detailed strategy that covers what to do before, during, and after a malware intrusion. This should include steps for:
- Identifying that an attack is happening.
- Keeping the disruption contained to limit the damage.
- Figuring out the amount of damage it caused.
- Let everyone who needs to know about it, like employees and customers, understand what’s going on, and the process of normalizing things after.
Keeping the Plan Updated
- It’s imperative to regularly check and improve the plan to make sure it works well.
- Also, practice using the method to see if it’s effective.
Setting up Communication Rules
- Decide the ways to tell people about the attack both -inside and outside the organization.
- Make it clear who will talk on behalf of the organization and how information will be shared.
Develop a Robust Data Backup and Recovery Strategy
A significant component of a ransomware incident response plan is a robust data backup and recovery strategy. That involves regularly backing up your organization’s details and storing them in secure offsite locations to protect against information loss caused by these damages; this is how to go about it;
- Backup Strategy
- Identify Pivotal Data: Figure out what data is most significant.
- Set Backup Frequency and Retention: Decide how often to back up and for how long.
- Consider Data Sensitivity and Rules: Think about how sensitive the data is and any regulations to follow.
- Automated Backup
- Use Automated Systems: Have some automatic input backup systems
- Pick Secure Solutions: Choose tools that encrypt information and check for integrity.
- Offsite Storage
- Keep Backups Elsewhere: Store copies of data in safe locations away from the main storage.
- Choose Cloud or Remote Centers: Consider using cloud services or remote centers for storage.
- Follow the Rules and Spread Locations: Ensure backups comply with regulations and are in different places
- Testing and Evaluation:
- Test Regularly: Check backup systems often to make sure they work.
- Simulate Attacks: Practice dealing with fake malware damage to see how well you can recover.
- Fix Problems: Improve any weak spots found during testing.
Prepare for Incident Response and Recovery
Prepare the organization for such events by developing detailed strategies and training the team. Conduct regular drills to assess readiness and improve processes. Build partnerships with cybersecurity experts, law enforcement, and incident response firms for support during intrusion.
Establish a communication system for informing stakeholders about incidents and response efforts. Stay updated on its trends and adjust defenses accordingly.
Do You Know?
With a cyber attack happening every 39 seconds on average, more than 8,00,000 people are a victim of it, each year.
Conclusion
In short, ransomware attacks are a huge threat to businesses. And to tackle them, businesses should plan. By following the steps in this guide, you check for risks, set clear rules, improve computer security, ideas for data backups, and be ready to respond to them.
Taking cybersecurity seriously is vital for businesses to keep input safe, operations smooth, and maintain trust in the digital age.