Streamlining User Experience_ A Guide to Implementing Single Sign-On (SSO) in Web Applications

In the current scenario of the digital landscape, web applications have become an integral part of our professional as well as personal lives.
To get access to the platform, it requires some form of authentication, which means users have to remember multiple passwords for various sites. However, it becomes complex as no one can memorize all the passwords, that’s when Single Sign-On (SSO) comes into the picture.
It is a centralized login system that provides easy access to multiple applications with just a single set of credentials. While it makes things easy for the end user, it also enhances companies’ security, because users are using their existing credentials. Also, learn about Website Insights For Business Success in this guide.
In this guide, we will give you comprehensive details regarding Implementation sso in web application, read further to know more!
What is Single Sign-On (SSO)
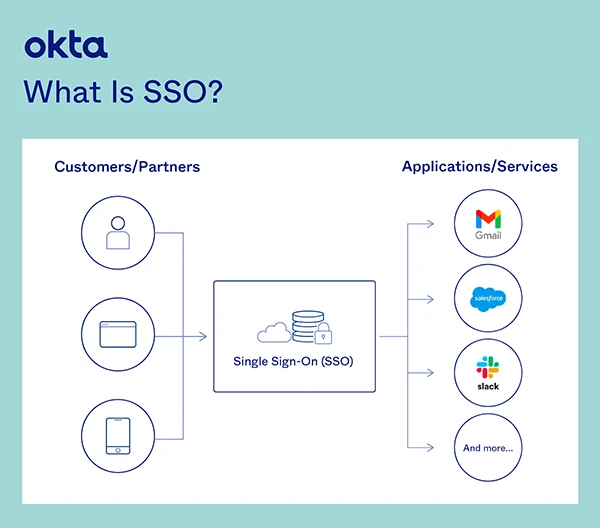
Single Sign-On (SSO) is a mechanism that provides a centralized login system, allowing users to log in once to multiple applications without any requirement to reenter the credentials.
SSO can be used by individuals and small and medium-scale companies for the management of multiple credentials.
Understanding the Working of Single Sign-On (SSO)
SSO work is based on the established trusted relationship between the application, which is a service provider, and an identity provider. The procedure works based on the exchange of certification between an identity provider and the service provider.
That certificate is used for the identification of information that is being sent from the identity provider to the service provider. In the context of SSO, such identity data takes the form of tokens and contains the identifying values of user information like email and username.
At the time of authentication, the application redirects the user to the server. In case the user is already authenticated, the server automatically redirects the user back to the application with an authentication token, usually a JSON Web Token (JWT).
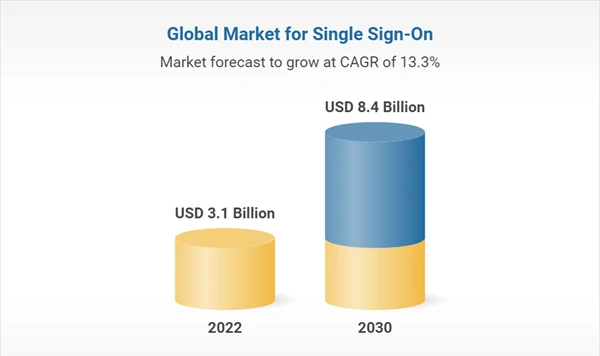
The below data represents the growing global market for Single Sign-On in the upcoming years.
Benefits of Implementing SSO
Implementation of SSO offers benefits like easy access to reductions in remembering multiple passwords, read further to know more in detail.
- No need for multiple passwords: SSO offers only a single set of passwords, which results in the strengthening of security and reduction of the need for multiple passwords.
In other words, users can create strong passwords instead of using easy ones that are less secure and used again and again.
- Smooth access to applications: With SSO, users can get access to all the platforms and applications easily, which will ultimately boost productivity. Plus it enhances the user experience as well with great efficiency.
- Better admin control: IT administrators get great control and visibility by using SSO, regarding what all types of applications and platforms are used in the company.
In addition, administrators can take the access back in case the user ends up losing the device. Also, by using SSO, IT departments do not have to spend their time on password recovery processes for multiple platforms.
- Enhanced security: SSO proves to be an effective tool for providing the best security, as it will reduce the need for users to remember multiple passwords. Also, admins can view and change the accessibility level easily, which results in the strengthening of security.
Did you know?
59% of users use similar passwords on multiple platforms.
Step-by-Step Implementation of SSO in Web Application
SSO server works as a single server, all web application providers trust this server and use it to access the login credentials. Let’s look through the implementation of SSO in web applications step-by-step.
Plan Out the Applications You Want to Associate with SSO
Pick out which applications need to be associated with the SSO structure. Go through the user login patterns and identify which users require access to which platform. You can create an SSO bundle for a set of applications, generally used by a group of users.
Check if your solution has in-built integration with the sites, and if it does not, prepare for development resources for the integration.
Integrate With Identity Provider (IdP)
Make sure that your existing identity provider is integrated with the SSO solution and test the integration as well. Ascertain the protocol that you will use to connect with the IdP, mainly Security Assertion Markup Language (SAML).
In case you want to go with an alternative, check for which external IdPs your SSO solutions support. Users typically log in via platforms like Google and Facebook.
Always Verify your Data in the Identity Directory
To use SSO solutions, you need to have authoritative and correct information about your user. Identities in IdP must be consistent with the ones used in the applications associated with SSO.
So you have to make sure that all the user’s data has up-to-date credentials and emails. Plus, through data identification, you can remove the old users who are inactive on the platform.
Evaluation of User Benefits
Consider evaluation of user privileges before implementation of SSO, to identify which user has access to which application. Most companies use the least user benefits rule, which means users get the least advantage using the functions.
So, it becomes important for you to analyze privileges carefully, based on a correct understanding of the organizational usage of each application.
Verify the Safety concern of the SSO System
SSO is a critical service and can turn out to be a failure for your systems. In case you are running the SSO server on-premises, make sure to set up redundancy and the server has suitable network and application security control.
Also, if you are using a cloud service, select it based on reliability and availability. Make sure that you have accurately configured the provider’s security options.
Best Practices for SSO Implementation
SSO implementation should be done using best practices, read further to get comprehensive details regarding execution.
- Secure Communication: Make sure that all the communication between IdP and SP happens using safe channels like HTTPS to protect sensitive information from tampering.
- Token Validation: Verify the token’s authenticity and assertion received from IdP, for prevention from unauthorized access.
- Logging and Monitoring: Always monitor authentication events and relevant data for troubleshooting and audit purposes. Also, promptly respond to any suspicious activities.
Conclusion
Implementation of Single Sign-On (SSO) in your web application allows users to access the platform securely with ease. By following the necessary points mentioned in this guide, you can enhance security, streamline the user experience, and also improve the efficiency of your application.