A Technical Guide on Strengthening Social Media Security Using Free VPN

As we progress rapidly in a technologically advanced age, online security is of prime concern for personal and professional use. Social media has become a relevant marketing and networking tool that can be secured by using a free VPN.
A complimentary VPN (virtual private network) may be a handy tool for protecting your internet identity. Moreover, it provides access to far-reaching geographical locations through its robust encryption system.
This article will prove a valuable guide for navigating the complicated world of Free VPN and their delicate interaction with social networks, phones, and online activities in this professional step-by-step guide.
Recognizing the Free VPN Market
Users may now enjoy safe and secure internet connections without paying, thanks to the growing popularity of free Virtual Private Network services.
These services dramatically increase internet privacy by encrypting data and masking your IP address, making it more difficult for hackers to intercept and exploit personal information.
It creates a safe virtual environment globally without distractions of speed, errors, and cyberattacks.
Step 1: Establish a Secure Social Network Connection
Opting for a trustworthy no-cost VPN service is the first step for an American reader looking for complete social media protection.
The initial phase is downloading and setting up the opted Virtual Private Network software on the computer, tablet, or smartphone.
After installation, the software acts as a go-between for a device and the community networking site, protecting and obscuring internet activity.
Step 2: Creating an Encryption Tunnel
All data is encrypted and sealed behind a virtual tunnel when activating an inexpensive Virtual Private Network, making it unintelligible to anybody listening in.
The communications with community networks will stay private thanks to this encryption, which keeps the personal information safe from prying eyes.
Step 3: Getting Around Geographical Limitations
Overcoming geographic limitations is one of the fantastic qualities of accessible virtual private networks. Social networking sites frequently use actual location to restrict content access.
You may safely converse with friends and colleagues around the world and access information that is limited to specific locations by using the electronic private network servers located in different regions to route the connection.
THINGS TO CONSIDER
No company, even a VPN, operates without funds, and therefore, it is significant to read the privacy policies to know how your personal data is used by any server for advertising and analytics purposes.
Security of Phone and Online Behavior
When considering using a local internet service provider or VPN, some alarming stats are relevant to study. Big businesses and even government organizations are susceptible to hacking, as is the entertainment industry.
In a recent survey, it was found that the healthcare sector proved the costliest, with 12 consecutive years of cybersecurity breaches. It cost an average of $10.10 million in 2022.
If you are using a mobile for video calls for physician consultation or an app for storing medical data, a VPN is necessary for securing records and payment methods.
In addition to providing security for internet network interactions, no-cost VPNs also shield phones and other online activity. This is how they go about it:
- Safeguarding Voice and Text Messages: It is nearly difficult for someone to overhear or eavesdrop on communications when using a trustworthy free Virtual Private Network to encrypt texts and phone calls.
- Preventing Data Harvesting: The no-cost VPN’s encryption strengthens internet activities like surfing, shopping, and email correspondence by shielding private data from possible data harvesters.
- Protecting Yourself From Cyber Attacks: Free virtual private networks are a strong barrier against cyberattacks, including DDoS assaults and hacking attempts, in a growing hostile digital environment.
- Safely Engaging on Networking Sites: With a private network, it becomes safe to use emails, protect social media credentials, and banking, and secure valuable passwords.
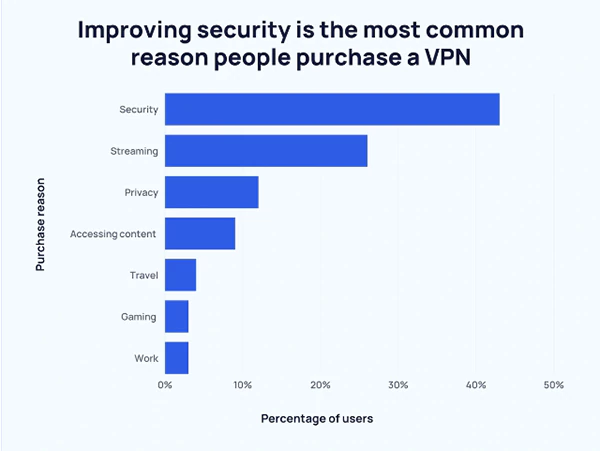
The graph below is a clear indication that improving security is the number one reason for using VPN, and therefore stricter government regulations are required to improve cybersecurity for all online work.
Conclusion
I need to appreciate social networks’ pervasiveness and indispensable significance in our lives as American readers. It’s a wise decision to include costless software programs in your social media security plan.
Strengthen your digital presence by safeguarding phone and internet activity, and confidently navigate the complex virtual environment by taking the actions above.
Also, manage your digital footprint by using no-cost online networks, which act as gatekeepers to a private and secure Internet environment.
Remain knowledgeable, maintain composure, and accept the power of free VPNs to protect your online activities.