Crucial Steps For Robust Mobile Application Security Protocols
Considering how mobile apps have taken over the tech world today, strong encryption protocols are needed.
Their security is an emerging big issue because of the common usage of smartphones and tablets by software programmers and consumers.
Consequently, this paper sets out to discuss some major steps in establishing and maintaining robust encryption parameters for mobile apps.
Incidentally, mobile application security entails a combination of approaches that blend numerous techniques and strategies to protect from emerging threats.
Ranging from threat assessment and secure coding practices to authentication mechanisms and regular testing, each step is important in creating a safe app ecosystem.
It must be prioritized as there has been continuing change in the landscape of mobile technology to maintain the integrity and dependability of such applications.
So let us understand the application security and evaluation of their threats through this article. Also, learn about Mobile App With Visual Testing in this guide.
Understanding Application Security
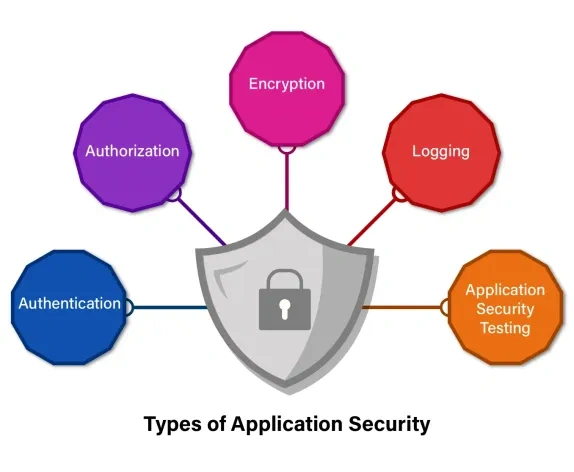
It is vital to understand what application protection means before we embark on specific protocols.
Application security refers to measures that enhance the safety of mobile apps during their lifecycle.
It embraces different techniques and strategies used to protect apps against challenges like malware, data breaches and unauthorized access attempts.
The approach includes taking into consideration privacy concerns throughout an application development lifecycle starting from the initial design, and coding to deployment and support.
With this in mind, developers can apprehend prospective vulnerabilities at an early stage to take proactive measures.
This helps to avoid long-term secure and reliable applications that could be exploited.
Evaluation Of Threats And Analysis Of Risks
Developers must spot various possible threats along with their app’s weaknesses that may be liable to compromise its soundness.
This includes assessing the architecture of the app, its functionality, and how it handles data for identifying possible spots where it may be weak.
Developers might use different tools alongside methodologies during this process to evaluate an attack surface of their applications as well as find out would-be points through which hackers can enter into them.
So developers should know what sort of threats or vulnerabilities they have so that they can direct their attention to them.
Secure coding practices
Security threats in mobile applications require that programmers observe safety measures in coding practices.
To neutralize these risks, the code writers should follow the best practices known in the industry.
Encryption as well as input validation can also be used in the development of a system that would guarantee the safe transmission of information.
Authentication & authorization mechanisms
Robust authentication and authorization mechanisms should be implemented for mobile applications to control access and protect confidential information.
To authenticate users’ identity securely during logins, biometric authentication or multifactor authentication is required as a part of this process.
In addition, developers should put in place strong authorization controls to restrict user’s access based on their positions in the system.
Data encryption & storage
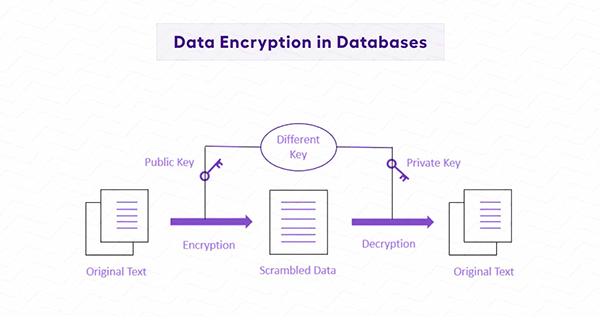
Confidentiality and integrity are preserved in mobile apps via data protection measures both when data is stored on devices and in transit.
Additionally, software developers must use strong cryptographic algorithms when securing sensitive data stored on devices, since this prevents unauthorized access in case the device is stolen or compromised.
Moreover, all communication between the application client side and backend servers should be encrypted via secure protocols to avoid peeping tampering.
Secure network communications
Smart phone applications, in most cases, rely on network communications to link with backend servers and external services.
This sort of communication has to be secured to avoid potential data interception as well as man-in-the-middle attacks.
Therefore, programmers are required to implement secure communication protocols that help encrypt the exchanged data over networks while also validating server certificates to ensure the authenticity of endpoints.
Regular security audits and testing

A long-lasting web app security can only be maintained through ongoing processes that involve monitoring, auditing, and testing.
Aside from that, developers should also consider conducting regular system audits to locate any new susceptibilities or weaknesses that may have arisen since its inception.
Moreover, extensive penetration tests and vulnerability assessments need to be conducted for purposes of simulating real-life attacks.
Additionally, extensive penetration tests and vulnerability assessments must be carried out to simulate real-life attacks as well as test the efficacy of present privacy controls.
User education and awareness

Lastly, users of phone applications need to learn about best practices in protecting such apps, which can only lead to creating a safe environment.
As part of this process, developers should come up with clear guidelines on how one can safely use their application, including advice on generating strong password.
By doing so, they can make users become enlightened enough thus enabling them to take proactive measures to protect their data and privacy.
Security patch management

A flawlessly managed secure patch is a very important component of mobile application security protocols.
Developers have to be on constant alert for any signs of weak points in the program and therefore be able to address it as early as possible.
This involves keeping up with technical advisories and updates shared by relevant sources such as libraries and frameworks applied in the app.
Rapid fixation of known vulnerabilities minimizes risks associated with exploitation that can be made by malicious actors thus ensuring that the application remains secure.
Incident response planning
No application, however fortified, will ever escape security incidents altogether. Consequently, there should be an incident response plan aimed at effectively managing and mitigating such breaches when they happen.
The developers need to have clear guidelines on how to detect privacy breaches, contain them, and recover from them including communication protocols, escalation procedures, post-incident analysis etcetera.
By planning for possible threats before they come, developers can minimize user impact as well as brand damage caused by this application.
Compliance with regulatory standards

Besides technical safety measures deployed in these apps, they must also conform to pertinent regulatory standards and industry regulations.
Considering the type of application and its data processing, various compliance requirements such as GDPR, HIPAA or PCI DSS may apply to developers.
To comply with these standards, proper security measures must be put in place by having audit trails and following specific data handling and user privacy regulations.
Compliance prioritized helps demonstrate their commitment to protecting users’ data, as it avoids any possible legal or financial consequences.
Conclusion
To sum up, ensuring that solid mobile application security protocols are in place is crucial for protecting confidential information and guarding against potential menace.
Developers can build trust among users regarding the safe operation of an app by using this article’s essential steps.
From risk assessment processes plus coding securely to authentication methods including frequent testing respectively, each step is important when developing a secure smart device app environment.
As technology expands its frontier on mobiles, safety remains key towards maintaining the WI-FI-enabled devices’ credibility and stability.
