How does QR code technology work?
With a 94% increase in interaction from 2018 to 2020, QR codes have become an integral part of our lives, and that all just happened overnight.
QR codes are literally everywhere, from cereal boxes, and restaurant menus to payment links. It works as a gateway to broader information and services in just the blink of an eye. Also, learn about the Platform for Technology in this guide.
QR technology can be categorized into static and dynamic QR code, which industries have been leveraging to provide a more seamless and secure connection for customers.
So, in this comprehensive guide, I will walk you through literally everything on QR technology, how it works, and how you implement a secure QR code.
But First, What Exactly is a QR code?
Short for quick response, QR refers to a machine-readable optical image, which is usually a black-and-white pixelated image. This is a convenient way to store and access data, which can be read by using an imaging device such as a camera.
Additionally, QR code tracking ensures proper encryption and destination tracking. This also allows businesses to gather some valuable insights into their customers’ behavior that helps them curate a more personalized experience.
As technology has matured, QR codes have been providing new ways to engage customers. It lets you:
- Send and receive payments.
- Get a detailed description of some products and services.
- Check the menus in restaurants.
- Get directions on Google Maps.
- Verify login details.
- Access Wi-Fi by storing passwords.
Did You Know?
According to Gartner, 80% of commercial activities will be contactless by 2024 and will be replaced by QR technology.
What’s The Difference Between Static & Dynamic QR Codes?
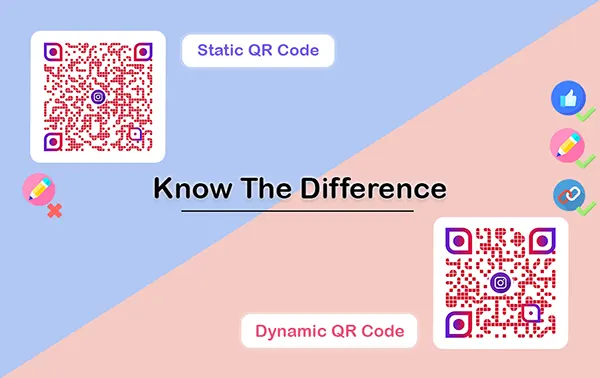
QR codes can vary in their designs and functionality, But they usually fall into the static and dynamic QR codes.
Static QR code: A static QR code stores data directly onto the pattern. It has a fixed destination that cannot be modified after the data is live, and whatever information is attached to it will remain forever.
The information is usually encoded within the alignment of these pixelated patterns, and not somewhere in the back-end. This is why the bigger the data, the more modules it would require, leading to a congested QR pattern.
Dynamic QR code: Dynamic QR, on the other hand, is a more advanced form of storing data, and it allows you to change and update data even after the generation of the actual code.
It can accommodate more data types when compared to the static QR codes and lets you store more data, again doesn’t define the number of modules in your pattern.
Here is a proper table to figure out the differences between static and dynamic QR codes:
| Static QR Codes | Dynamic QR code |
| It cannot be edited after the generation | It can be edited or modified even after the printing |
| Cannot be used for retargeting the audience | It can be used to repurpose the previous audience |
| This does not offer QR scan tracking | QR scan tracking & analytics are available |
| It comprised of long and complicated URL | This consists of a concise URL |
| Take longer to scan the pattern | It takes less time when compared to the static QR code |
| It has a fixed destination and cannot deliver different campaigns | It can deliver different campaigns based on the schedule |
So, How Do QR Codes Work?
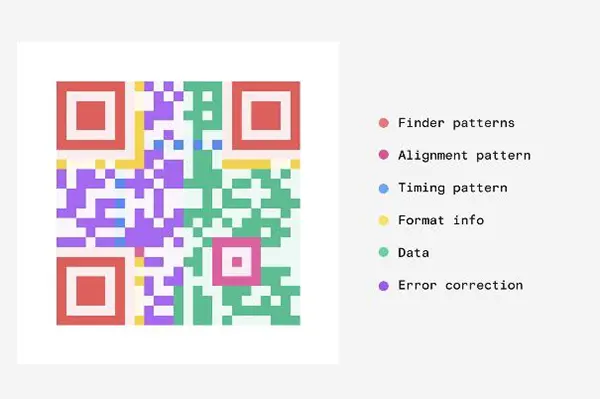
A QR code is a machine-scannable image consisting of black squares and dots, each representing a piece of information. And after the pattern is scanned, it translates into the human-reliable content
This allows businesses a secure and innovative way to interact with their customers. Also, businesses have been solidifying QR codes as a powerful tool for building trust and credibility in the user’s experience.
Here’s a complete breakdown of the QR code structure:
- Quiet zone: This is an empty white border outside the QR code.
- Alignment pattern: A small square near the bottom-right corner ensures the pattern can be read, even from an angle.
- Hinder pattern: Three large squires outside the QR code, once it identifies the squires it knows everything contained in the pattern.
- Timing pattern: An L-shaped square that makes damaged QR codes readable.
- Version information: Version information as the name suggests identifies which version of the QR is being read.
- Data cells: This consists of the rest of the pattern, containing the actual QR code information.
Are QR Codes Safe?
Well, QR codes are not inherently dangerous, but the links they contain can be hazardous sometimes. Where a QR code’s URL can take you to a phishing website that may trick you into entering your personal information.
But in general, QR codes in supermarkets and restaurants are usually safe. Scanning those in open spaces like parks and stations might contain some unauthorized activity.
Also, do you know?
According to a study conducted by Ivanti, only 39% of customers can identify the malicious QR code.
Bottom Line
QR codes have become a critical adaptation in the modern environment. It enhances the customer’s experience by providing them more accessible access to information, and all that in just a few seconds.
However, the potential claims may include security concerns, as this makes it easy for intruders to get their hands on your valuable data.
