Unveiling the Power of Cloud Security: Safeguarding Your Digital Assets in the Cloud
Do You Know that in 2022 alone, there were about 5.4 billion malware and 4 out of 10 did result in some serious confidential data leakage?
And, this is why implementing a good security system is crucial, not only to secure your sensitive business information but also for your customer’s safety. So, what’s the perfect security system a business could turn into to safeguard its digital assets?
Well, Cloud computing is a range of methods, all designed to protect your business essentials in a cloud computing environment. Let’s unveil the power of cloud security and have a deep dive into how it can safeguard your digital assets.
Key Principles of Cloud Security
Understanding cloud security starts with familiarizing oneself with its core principles. So, here take a look at some of the key principles of cloud security:
Multi-layered security
Cloud security proposes multiple layers of security, where each layer is backed by the other. So if a hacker manages to breach one level of security, the other one steps in to provide the necessary protection.
This security system involves a range of components such as a firewall, intrusion detection systems, data encryption safeguards, or a strong password.
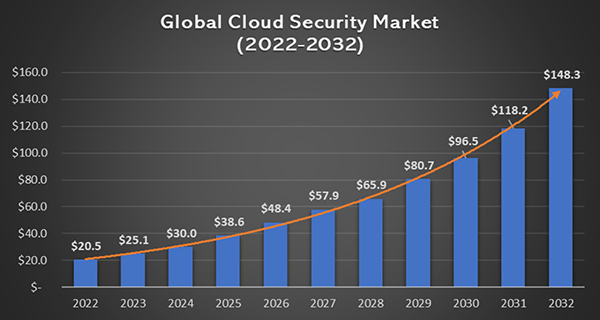
Data-Centric Protection
This level of security prioritizes data as the most valuable asset in the cloud. And, this is why it deserves the highest level of protection. This involves strategies like encryption, data masking, tokenization, and kind of DDoS mitigation to ensure that your valuable data never falls into the wrong hands.
Data Backup and Recovery Plans
Another core principle of cloud security refers to data backup, which makes sure that your data is always available to you, even in the case of a system failure or a cyberattack.
In addition to that, implementing a perfect disaster recovery plan ensures that your data will be safe and accessible even in the worst-case scenario.
Common Cloud Security Threats
Cloud security greatly enhances security management. But there are also some potential downsides to this system. Here are some of them:
- Data Breaches: A data breach refers to some unauthorized access to the critical business data stored in the cloud. This may result in weak access control and insider threats to the data.
- Service Interruption: Cloud services may sometimes lead to service interruption due to hardware failure, networking issues, or a cyberattack. This can lead to downtime, lower productivity, or some deep financial loss for an organization.
- Supply chain Attack: Cloud security is still vulnerable to cyberattacks. This is where some cyberbullies take advantage of poor security practices such as limited policy control, weak passwords, and overly-granted access.
Cloud Security Best Practices
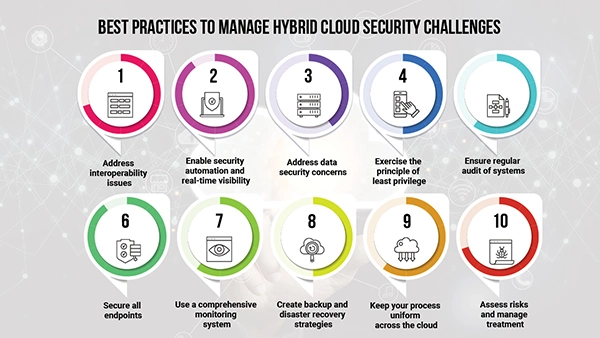
Cloud security leverages a range of strategies and techniques to provide you with some perfect data protection strategies. So, here take a look at some of the best cloud security practices:
- Risk Assessment: Conduct a thorough risk assessment to identify the potential vulnerabilities to your system. Assess the severity of these risks and then prioritize the organization’s resources based on their severity.
- A Zero Trust Security Model: Implement a zero trust model, both for the internal and external entities. Here you can have strict access control and the least possible access to the data to minimize the risk of unauthorized access.
- Encrypt Data: Implement a strong encryption mechanism for sensitive data of the organization to protect it from any unauthorized access.
- Employee Training and Awareness: Another major practice in ensuring a perfect cloud strategy is educating the employees about the potential risk and their critical role in maintaining security within the cloud environment.
Cloud Security Solutions
Now that you have a clear understanding on some effective cloud security practices. Here take a look at some of the best cloud security solutions.
- Cloud Access Security Broker: CASB is an optimal security tool that acts as a gateway between the user and the cloud service. These asses the risk associated with each service and then implement the policies according, while actively performing data encryption and malware protection.
- Cloud Security Posture Management: CSPM identifies the insecure configuration and then automatically straightens out vulnerabilities in compromised systems.
- Security Incident and Event Management: SIEM solutions help organizations detect, and investigate cyberattacks more effectively. This is a uniquely capable tool that also helps organizations cater to the vulnerability in the system. In addition to these tools, implementing thorough archive storage systems ensures ensures that critical communications are securely stored and easily accessible, further strengthening your overall cloud security strategy.
The Future of Cloud Security
As we move into 2024, cloud security is moving beyond the traditional IT boundaries. It is probably one of the critical concerns for every organization in a way to safeguarding their sensitive information.
But, do you know?
According to the Cost of a Data Breach Report 2023, almost 45% of the data breaches are cloud-based, while 82% of the breaches relate to data held in the cloud.
This significant rise in cloud-based threats indicates the major downside of this system, ensuring that implementing robust cloud security measures is no longer an option for businesses.
Conclusion
In closing, implementing some robust security measures is a critical component in safeguarding the sensitive digital assets of an organization. While the system is still not properly secure, it surely provides an edge over the regular on-premise security system, ensuring enhanced security while complying with the regulatory alignments.
Also Read: A Comprehensive Guide to Personal Injury Marketing
