Preventing Data Breaches: Best Practices For Organizations
Data Breach is an unfortunate practice where unauthorized personnel gain access to the confidential or private data of the organization.
There are countless reasons for that to happen, like intentional action for stealing the information of the organization. It could also be because of the accidental leak of private data by the employee.
Regardless, this could potentially risk the companies in several ways since their data such as bank and transaction details have been exposed. As there’s been an increase in such cases, many are opting for an online masters cyber security degree.
Wondering how to prevent this from happening? Then stick till the end to find your answers. So, let’s get started!
Top 5 Practices To Prevent Data Breaches In Organizations
As organizations are rapidly switching to digital storage space for saving enormous amounts of data, the risks have increased with time.
Although encryption is an important aspect of securing the data, there are several other practices to prevent from being vulnerable to such risks.
Learn about the top 5 practices to prevent data breaches in organizations that are listed below:
Cybersecurity Awareness Training
The most crucial factor for every organization is guiding and training its workforce assets to streamline its business and prevent data breaches. Since it is the employees who are first of defense when it comes to protecting sensitive data.
Just investing in data protection tools and programs is a waste of money unless the employees are trained to handle them as well.
Thus, having cybersecurity awareness training is crucial for teaching employees about how data breaches occur. They will also learn about the ways that the hackers can trick them and divulge into the private network credentials:
- Social engineering
- Phishing
So, teaching employees how to detect and respond to cyber threats will equip them to avoid such situations. This can protect several businesses from going into ruins.
DID YOU KNOW?
A report released by Keepnet Labs indicates that cybersecurity awareness training has led to a 70% reduction in cybersecurity-related risks in 2024!
Strong Passwords

Considered to be one of the best practices among cybersecurity measures, having complex and unique passwords is the best solution.
Having strong passwords can be a game-changer since it is difficult for cybercriminals to guess or crack them. Although it may seem like a hassle at first, it is worth the effort and time taken.
Now if you are wondering how to effectively manage them, then do not worry we have got your back! Since it is a critical aspect, it shouldn’t be overlooked.
If you are not good at remembering passwords, then use a password manager to secure all your passwords in one place at a go!
NOTE: To ensure that your password strength remains high, avoid using common words or phrases. Instead, use a combination of letters, numbers, and symbols to make it complicated for the hackers who are attempting to crack it.
Data Leak Management
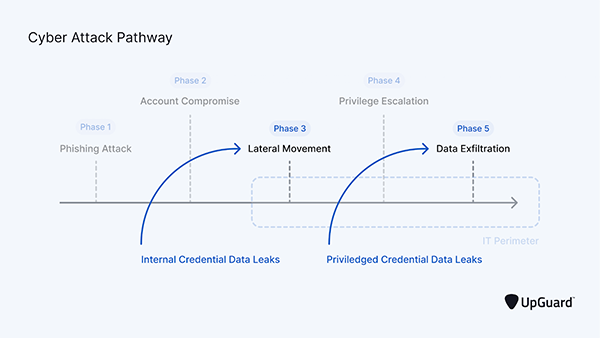
Data breach is an unfortunate event that has increased over the years due to several reasons. One of them is the lack of implementation of practical strategies such as data leak management.
Such intrusions can expose the credentials that were meant to be kept private, making the organization vulnerable. Data leaks are like golden opportunities for cybercriminals to take control of phase 4 of the cyberattack pathway.
Thus, having efficient data leak management is essential to protect companies from becoming victims of dark web data hosts.
All you need to do is take 2 of these aspects into consideration while looking for a solution:
- Third-Party Data Leaks
- False positives
DID YOU KNOW?
According to a report released by IBM in collaboration with the Ponemon Institute, the victims who respond to the data breaches within 200 days, spend at least $1.1 million less compared to those who don’t!
Internal Security Vulnerability Management
Data breaching isn’t just a process of hacking the documents, it is the internal security vulnerabilities that act as the contributing factor. These vulnerabilities could range from open ports to typosquatting susceptibility.
Detecting these threats is of the utmost priority for any organization, so using the collaborative efforts approach can help. This can be done by using risk or security assessments and security ratings.
But what does security ranking mean? With the scores ranging from 0 to 950, they are the objective qualitative measurements to understand the security posture of any organization.
With this, it becomes easier to make strategies for ensuring the utmost security of the stored sensitive data.
Regular Monitoring & Control Access

Keeping an eye is always crucial to ensure the safety of the collection of sensitive data that is preserved by the organizations. Monitoring and controlling access to the data are regarded as the most reliable way to keep an eye on the data.
For this, you can always implement centralized authentication mechanisms and control lists for security reasons.
This ensures that only authorized personnel access the critical documents and data that are related to the organization.
Thus, it allows you to monitor the documents in real-time and learn about the recent network activities. This makes it easier to detect suspicious activities and respond accordingly.
DID YOU KNOW?
According to a report released by IBM Security, 51% of organizations plan on increasing their investments in cybersecurity! This includes incident response (IR), planning and testing, employment training coupled with threat detection & response tools.
Overall Inputs
With the ongoing digitalization, the risks and cases of data breaches among organizations are not something unheard of. However, the risk rate of the same has increased by 15%!
This draws attention to the importance of foolproof measures to prevent data breaches. You can achieve that by following the best 5 practices listed above and save your organization from being vulnerable to such factors.
Also Read: Effective Communication Tactics for Remote Teams
