The Role Of Access-Managed Switches In Network Security

Networks are the indispensable foundation of modern communication, powering seamless data exchange for businesses worldwide. However, in today’s rapidly evolving cybersecurity landscape, organizations face an unrelenting barrage of threats.
The numbers speak for themselves: global cybercrime damages are predicted to reach a staggering $9.5 trillion in 2024, an alarming indicator of the escalating risks. (Source: Cybercrime Magazine) This stark reality underscores the critical need for robust network defenses.
Enter access-managed switches – often the unsung heroes of network security. As cyber threats become more sophisticated and pervasive, access-managed switches emerge as essential guardians, enabling organizations to navigate the intricate world of cybersecurity with confidence, ensuring the resilience and integrity of their network infrastructures.
This article provides insights into the critical role of access-managed switches, dissecting their complex functions in fortifying network security and empowering businesses to stand strong against an ever-growing tide of digital dangers.
KEY TAKEAWAYS
- Access-managed switches provide significantly more control, visibility, and advanced security features compared to basic unmanaged switches.
- VLANs allow administrators to logically divide a physical network into isolated segments, enhancing security by limiting lateral movement in case of a breach.
- ACLs enable granular control over network traffic, allowing administrators to define specific rules for permitted or denied access based on various criteria.
- QoS prioritizes critical network traffic, ensuring consistent performance and a more reliable communication environment, even during congestion.
- Access-managed switches offer robust monitoring tools and logging capabilities, enabling real-time insights into network performance and proactive identification of security anomalies.
- Support for secure protocols like SSH and HTTPS ensures that remote management of switches is encrypted, protecting sensitive configuration data from eavesdropping and unauthorized access.
- Regular firmware updates are crucial for patching security vulnerabilities and introducing new features, while built-in vulnerability management tools help identify and mitigate weaknesses.
What Are Access Managed Switches

Access-managed switches, which are also known as managed switches, set themselves apart from their unmanaged counterparts by allowing network managers more visibility and control.
Managed or access switch offers many configuration opportunities and sophisticated functionality, at the same time unmanaged switches function independently. The operating system with all of these switches enables administrators to modify the network configuration to satisfy needs.
How Access-Managed Switches Help In Network Security
See the componenets of access-managed switches along with their roles through this infographic attached below:
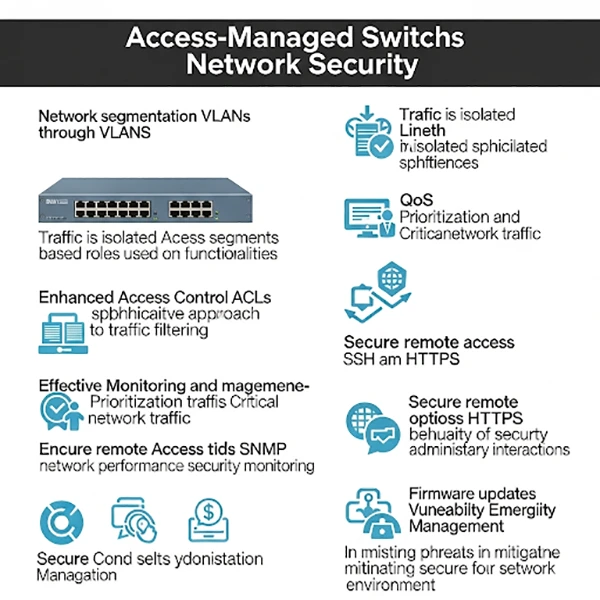
1. Segment The Network Security
One of the most powerful features of access-controlled switches is their ability to create Virtual Local Area Networks (VLANs).
Network administrators can divide the network into separate, isolated portions thanks to VLANs, even though they are physically connected to the same switch. By restricting device-to-device connectivity, this segmentation, modifies security by reducing the possible impact of a security breach.
Computers in the finance and marketing divisions, for instance, may be located on separate VLANs. If a device inside one VLAN is compromised, there is much less chance of lateral movement to other VLANs.
Access-managed switches provide a dynamic and scalable network security method by allowing administrators to remove, add, and alter VLANs as needed.
2. Enhanced Access Control Lists

Access Control Lists, or ACLs, are another crucial tool that access-managed switches offer in addition to other essential tools for network security.
With the use of ACLs, administrators may create rules that specify which devices are permitted or prohibited from obtaining specific network features. With this degree of control, a company may limit who has access to the system while yet protecting against different kinds of online attacks.
For example, an ACL may be set up to limit access at particular times of the day or to reject traffic from particular IP addresses.
3. Prioritizing Traffic Using Quality of Service (QoS)
Networks commonly carry a variety of traffic types, ranging from VoIP calls and real-time video conferencing to emails and file transfers. Quality of Service (QoS) features on access-controlled switches enable administrators to prioritize some types of traffic over others.
This ensures that critical applications receive the necessary bandwidth and minimal latency, even during times of network congestion.
QoS is significant in terms of security regarding voice and video communications. Access-managed switches contribute to a more dependable and secure communication environment by prioritizing certain sorts of traffic. This is mainly crucial in firms where regular communication is important to day-to-day operations.
USEFUL FACT
Phishing remains the most common cybercrime, with approximately 3.4 billion fraudulent emails daily.
4. Offer Effective Monitoring and Management Tools

Administrators can keep a close eye on network traffic thanks to the robust monitoring and management capabilities provided by access-managed switches.
Real-time monitoring of traffic patterns, switch performance, and any issues is made possible with support for SNMP (Simple Network Management Protocol). By proactively detecting and resolving abnormalities with SNMP, administrators may help build a more robust and secure network infrastructure.
Moreover, logging and reporting tools are frequently come with logging and reporting features that let managers review historical data and track changes in network traffic.
This retrospective analysis can be quite helpful in identifying patterns suggestive of security issues, allowing for prompt action and mitigation.
5. Secure Remote Access with SSH and HTTPS
Remote management of network equipment is a standard necessity in today’s interconnected society. Access management switches frequently offer secure protocols for remote access, such as SSH (Secure Shell) and HTTPS (Hypertext Transfer Protocol Secure).
Through the encryption of communications, these protocols reduce the possibility of unwanted access and eavesdropping in on conversations between switches and administrators.
Because SSH encrypts the whole interaction, it provides a secure alternative to traditional telnet. HTTPS safeguards sensitive data transmitted during tasks like configuration and monitoring by guaranteeing that web-based management interfaces are reachable over a secure, encrypted connection.
6. Facilitate Firmware Updates and Vulnerability Management
Access-controlled switches are essential to network security, as they make it easier to apply firmware updates on time. Regular updates reduce the likelihood that bad actors will exploit them by fixing known vulnerabilities and adding new features and enhancements.
Furthermore, managers can assess the security posture of their network infrastructure with the help of vulnerability management features commonly included in access-managed switches.
These tools can detect and document weaknesses in the switch’s firmware, which helps create effective risk-reduction plans.
Conclusion
The access-controlled switches are a great tool for ensuring network security. Because they offer granular control through VLANs, prioritize important traffic with QoS, enforce access restrictions using ACLs, and provide secure remote administration tools. As a result, these technologies should be incorporated into modern cybersecurity methods.
Ans: Unmanaged switches are plug-and-play for basic connectivity; access-managed switches offer extensive configuration, advanced security, and remote management.
Ans: VLANs logically segment networks, isolating traffic and limiting the spread of breaches by preventing unauthorized access between segments.
Ans: ACLs are rules on a switch that permit or deny traffic based on attributes like IP or port, controlling device access to network resources.
Ans: Firmware updates deliver critical security patches for vulnerabilities and introduce new features, protecting devices from cyber threats and ensuring stability.
Ans: No, they are one component of a broader cybersecurity strategy. Comprehensive protection requires firewalls, IDS/IPS, endpoint security, and strong policies.
