The Future of Network Security: A Guide to Zero Trust Network Access
Network security is a hot topic in the world of cybersecurity today as businesses try to simplify the network access process but never compromise the safety of the corporate network.
But with the emergence of remote users, security is not more complicated than ever as it requires its own set of practices to ensure secure remote access. This is where Zero Trust Network Access (ZTNA) comes in.
ZTNA solutions, a new front in the world of security, will define the management processes in the coming future. This new approach proves to be more effective than anything we’ve known to date, so let’s get into learning everything about it.
Understanding Zero Trust Network Access (ZTNA)
By now, all traditional solutions have considered that the risks to a network would only come from the outside, and everything within the system was considered “friendly.” However, there were two main safety gaps in this approach.
First, it eliminates the potential for internal threats rooting from users having access to the resources without any control.
Secondly, it belongs to another era where the perimeter of a corporate system was clearly defined, unlike now.
Now, we have organizations with a remote workforce that need to create user connections from around the world. Remote employees work from anywhere, so we don’t have a set perimeter anymore.
So how does Zero Trust Network Access challenge this notion of a trusted internal network? Well, ZTNA operates on the principle of “never trust, always verify.” Unlike conventional models that rely heavily on perimeter defenses, it adopts a holistic and dynamic approach to safeguarding networks. It assumes that threats may originate both externally and internally, necessitating a comprehensive stance.
Plus, it focuses on the identity as its perimeter, so it takes security to the doorsteps of the actual users. Each user attempting to access resources goes through a strict authentication process and is treated as an unfriendly source until proven otherwise. This approach both reduces the risk of unauthorized users gaining access to resources and aligns with the modern reality of cloud access and vague perimeters.
As we start to understand the fundamentals of the security model, it becomes clear that this is not only a set of tools to implement granular controls through the entire system. It is also a mindset that shapes policies to be more vigilant.
Key Components of ZTNA
When you ask “What is ZTNA?” It is paramount to understand that Zero Trust Network Access is not a tool or a security service by itself, but a convergence of several approaches and policies that reinforces an organization’s security posture. So let’s see some of these components.
User Authentication
At the core, everything goes through a rigorous authentication process. All users have their privileges according to their roles, but in order to access these resources, they need to provide a set of authentication. This is asked continuously and includes more than just a password, often we see advanced tools such as MFA.
Network Segmentation
Reducing the attack surface is a decisive part of a zero-trust architecture. By segmenting a big network into its small components, you can prevent potential attackers from moving laterally within the network and quarantine the attack before it spreads further.
Continuous Monitoring
Unlike traditional models that rely on periodic checks, ZTNA adopts continuous monitoring. This involves real-time analysis of user behavior, device health, and traffic patterns. Any deviations from established norms trigger immediate responses, enabling proactive threat detection and mitigation.
Least Privilege Access
In this model, users are not granted access to a whole system, but instead, they follow a least-privilege approach. This means that every user only has access to the resources primarily for their specific roles and nothing more. A least privilege approach reduces the risk of internal threats and minimizes the attack surface.
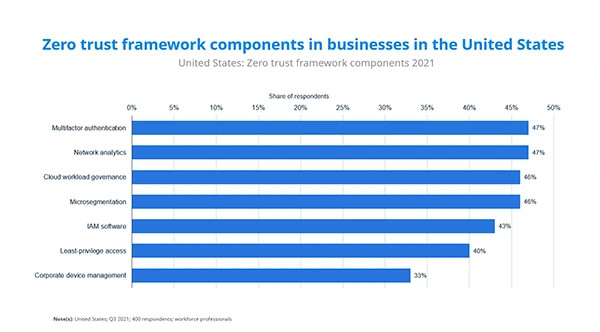
Percentage of Zero Trust framework components in businesses in the United States of America.
ZTNA vs Traditional Security Models
Traditional security models often focus on perimeter-based methods, suggesting that once inside a network, all the devices and the users can be trusted. This is the main problem with the traditional solutions, as they fail to keep up with the increased sophistication of today’s cyberattacks.
On the other hand, ZTNA asserts that trust should never be assumed, regardless of the user’s location or the device’s origin, thus challenging the standard trust model. It has a “never trust, always verify” stance, in contrast to typical methods, which concentrate on protecting the perimeter.
It acknowledges that risks can come from both internal and external sources, calling for a thorough strategy that gives continuous authentication, micro-segmentation, and dynamic policy enforcement a top priority.
Implementing ZTNA: Steps and Considerations for Businesses
Implementing ZTNA requires a systematic approach and a well-planned process to ensure full functionality and high-level security.
Assess Infrastructure and Define Access Policies
Before implementation, conduct a thorough assessment of the existing network architecture. Then, clearly define policies based on the principle of least privilege. Tailor permissions to specific roles and responsibilities, aligning access with job functions to minimize the risk of unauthorized entry.
Select ZTNA Solutions
Choose solutions that align with your organization’s needs. Evaluate options for identity verification, micro-segmentation, and continuous monitoring to create a tailored ecosystem.
Employee Training
Train your employees on the importance of the Zero Trust Network Access model and its principles. A well-trained workforce on modern security is pivotal to the solution’s success.
Monitor and İterate
Continuously monitor the performance and effectiveness. Iterate policies and configurations based on evolving threats and organizational changes.
Overcoming Challenges in ZTNA Implementation
There are significant challenges in ZTNA implementation. User resistance to the change in access methods is one major obstacle. In order to get around this, companies should place a high priority on thorough user training that highlights the advantages of increased safety. Difficulties in integrating with current applications and systems are another common challenge.
These problems can be minimized by working with vendors, implementing a phased deployment plan, and conducting extensive compatibility tests. Moreover, organizational cultural changes could be necessary to adjust to its dynamic character.
Overcoming these deployment obstacles and guaranteeing its ongoing efficacy requires creating a proactive cybersecurity culture and encouraging constant communication.
How ZTNA is Shaping Network Security Trends
Zero Trust Network Access (ZTNA) is reshaping security trends by establishing a new standard for dynamic and adaptive protection. The move from perimeter-centric models to identity-centric approaches is gaining prominence.
Its emphasis on continuous monitoring, micro-segmentation, and least privilege access aligns with evolving cybersecurity needs.
